Lightweight Directory Access Protocol (LDAP) allows for authentication against a directory service, such as Active Directory (AD), meaning users don’t have to be manually added in the Web Application Manager organization. Instead, you can use one central repository of user credentials (your LDAP provider).
For more information on LDAP, see https://en.wikipedia.org/wiki/Lightweight_Directory_Access_Protocol.
When a user attempts to login to an organization that’s configured to use LDAP authentication, Sencha Web Application Client prompts the user to enter their credentials (Login Name and Password), as stored in the LDAP provider.
Once successfully authenticated for the first time, the user’s basic details (for example First Name, Last Name, Email Address) are copied from the LDAP provider in to the organization within Sencha Web Application Manager. The user is also assigned to the Default group inside of the organization.
LDAP Settings
To enable LDAP authentication support in Sencha Web Application Manager, select LDAP in Sencha Web Application Manager > Settings > Authentication.
You then need to specify certain details from your LDAP provider, to enter in to the Authentication Configuration screen. These settings are described below and illustrated in the following screenshot.
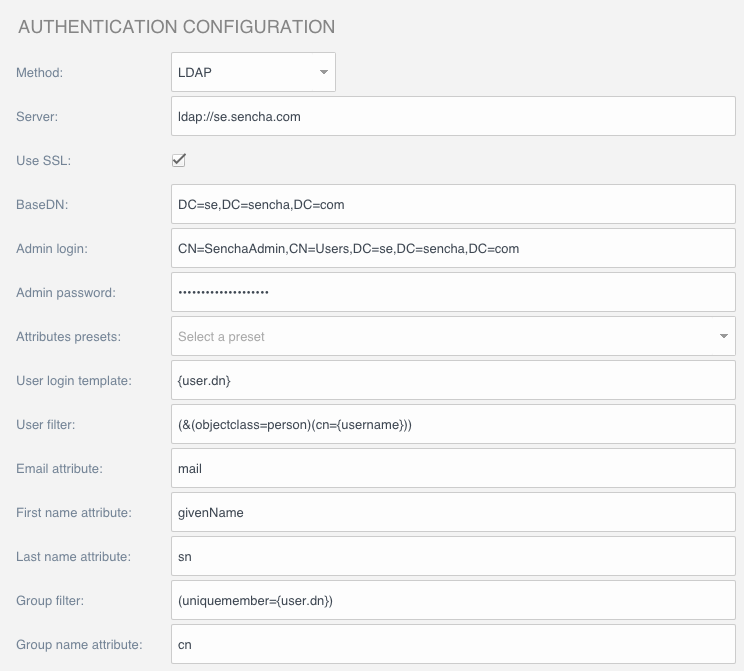
Server
The URL to send the LDAP authentication requests, for example: ldap://se.sencha.com.
Use SSL
Sets whether authentication requests will be made using a secure connection (over port 636) or a standard connection (over port 389).
BaseDN
The BaseDN is your LDAP provider’s domain described in a Distinguished Name (DN) format, for example: DC=se,DC=sencha,DC=com.
Admin login
This is the Distinguished Name (DN) of a user account that has administrative rights on the LDAP provider, and will be used when processing authentication requests for validating users, for example:
CN=SenchaAdmin,CN=Users,DC=se,DC=sencha,DC=com
Tip: If using Active Directory, the command line dsquery user can be used on a Windows server to locate a user’s Distinguished Name (DN), along with the Administrative tool ADSI Edit.
Admin password
This specifies the password for the Admin login, as defined above.
User login template
Defaults to {user.dn}
User filter
Defaults to (&(objectclass=person)(cn={username}))
Email attribute
The name of the attribute containing a user’s Email Address. Active Directory’s default is mail.
When a user authenticates with Sencha Web Application Manager and the LDAP provider for the first time, the user’s Email Address is copied across in to the organization.
First name attribute
The name of the attribute containing a user’s First Name. Active Directory’s default is givenName.
When a user authenticates with Sencha Web Application Manager and the LDAP provider for the first time, the user’s First Name is copied across in to the organization.
Last name attribute
The name of the attribute containing a user’s Last Name. Active Directory’s default is sn.
When a user authenticates with Sencha Web Application Manager and the LDAP provider for the first time, the user’s Last Name is copied across in to the organization.
Group filter
Defaults to (uniquemember={user.dn})
Group name attribute
Defaults to cn
