Sencha Web Application Manager’s primary focus is its rigorous attention to security. Sencha Web Application Manager serves enterprises and their employees, IT administrators, and application engineers. These environments have very strict information security policies and practices. This document details Sencha Web Application Manager’s security model.
Security Goals
Encryption is one of the first things one thinks of in “security,” but in reality data encryption is merely one slice of the security pie. The security model of Sencha Web Application Manager is unique from the traditional web, desktop, and mobile security models, in that Sencha Web Application Manager balances the challenging task of protection for the organization, the organization’s users, and the users’ devices with flexibility and ease of use, particularly for data synchronization and offline authentication.
Sencha Web Application Manager:
Ensures all user data and private organization data remains private and is not stored or transmitted in the clear or outside a user’s device.
Maintains oganizational control over the data that resides on a user’s device with the ability to remotely wipe the data at any time.
Maintains oganizational access control between applications, users and their devices. Sencha Web Application Manager provides clear insight and control over who uses a system, and when and where systems are used.
Provides access to private data offline with no real-time server authentication or authorization in place.
Sencha Web Application Manager always assumes it’s running in a hostile environment where the device is not necessarily in the hands of a trusted user. No device is considered a secure or trusted execution environment by default.
Mobile only: A portion of private data can potentially reside in web-based storage containers such as cookies or cache, and the browser must have these containers and files in the clear at runtime to operate. Sencha Web Application Client does not control the browser source code to secure these assets in real-time.
Sencha Web Application Manager handles these challenges:
- Local data encryption with secure key management
- Jailbreak and rooting detection on mobile devices
- Detect and disallow debugger attachment on mobile devices
- Configurable security policies for organizations
- Remote data wipe
Architecture
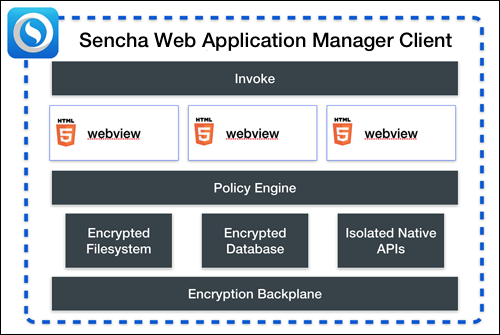
Applications: Each application has its own web view, isolating an application from all of the other applications running in Sencha Web Application Client.
Security Policy: limits what APIs each application can access.
Encryption Backplane: Low-level security library that handles the encryption of all persistent data.
Encrypted File System: All persistant data within Sencha Web Application Client is automatically encrypted before it is written to the application’s un-encrypted filesystem. Further each application has access to its own isolated encrypted file system via Sencha Web Application Client’s Secure File API.
Encrypted Database: Each application can be granted access to an encrypted database. An application can access this database via Sencha Web Application Client’s Secure Local Storage API.
Key Management
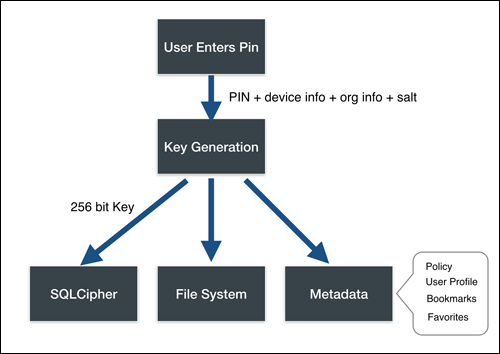
Sencha Web Application Client can be configured to require a security pass phrase or pin before granting access to the organization’s applications. For maximum security Sencha Web Application Client does not store the decryption keys in any persistent form. When the user enters their PIN, it is combined with other unique data to generate a decryption key. Once the decryption key is generated it is used to then decrypt the actual data. Without the user’s PIN the data cannot be easily decrypted without resorting to brute force decryption methods. Sencha Web Application Client can also be instructed to delete the organization’s data if too many incorrect pin entries are given.
Industry Standards
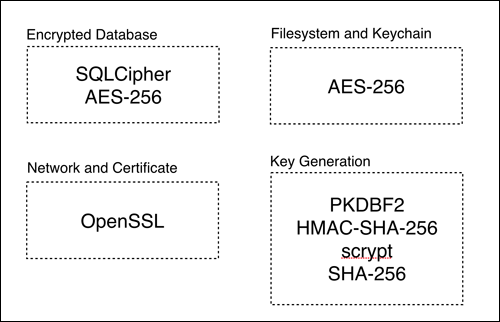
Sencha Web Application Manager relies on industry standard encryption and security algorithms and libraries. Sencha Web Application Manager uses AES-256, HMAC-SHA-256, SHA-256, PKDBF2, scrypt, OpenSSL, SQLCipher to ensure that data stored in Sencha Web Application Client is kept secure.
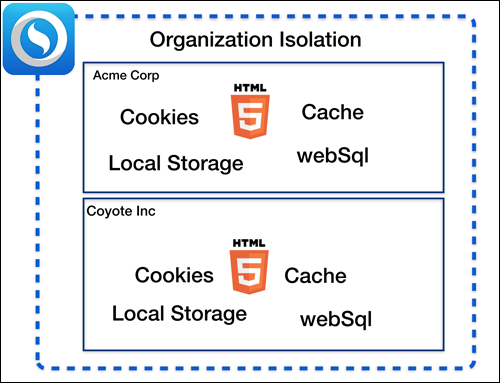
HTML5 local data
HTML5 applications can persist data on the client using cookies, caches, local storage and databases. In most browsers these assets are left unencrypted on the user’s device. In Sencha Web Application Client we solve this problem by encrypting all of this data. So by simply deploying your existing HTML5 applications in Sencha Web Application Manager the local information they store will be kept encrypted. Further because Sencha Web Application Client supports multiple organizations, the data from each organization is isolated.